Introduction to Access Control Models
When securing a property, whether digital or physical, controlling who gets in and out is crucial. Access control models are systems that manage this very process. They ensure that only authorized individuals can enter certain areas or access specific data. Imagine a key that only fits certain locks; access control models are like creating unique keys for different people based on their needs.
Access control is not just about locking doors or requiring passwords. It involves a set of methods that determine who is allowed to access information or locations. These methods can range from simple locks to advanced biometric systems. In the digital realm, access controls safeguard data against unauthorized access, protecting sensitive information.
There exist various access control models, each with distinct methods and permissions. These models cater to different levels of security required by an organization and the nature of traffic it handles. From basic systems for low-traffic areas to advanced ones for high-security zones, there’s an access model for every scenario.
Understanding access control models helps in making informed choices about security. It guides you in selecting a model that best suits your organizational needs. This post will discuss the four main types of access control models and help you understand their role in security management.
The Four Main Types of Access Control Models
Navigating the complex world of security can be daunting. Access control models form the backbone of security, determining who has the freedom to enter or access your property and data. Let’s dive into the main types of access control models to see how they differ.
Discretionary Access Control (DAC)
The DAC model is one of the simplest forms of access control. Property owners or specific users assign access rights to other users. This method is flexible and easy to manage, making it a good fit for smaller organizations or those with fewer restrictions on who should have access.
Mandatory Access Control (MAC)
In stark contrast to DAC, the MAC model operates on a strict rule-set. A central authority assigns clearance levels to all users and data. Users can only access information that matches or is below their clearance level. This model suits environments where security is a top concern.
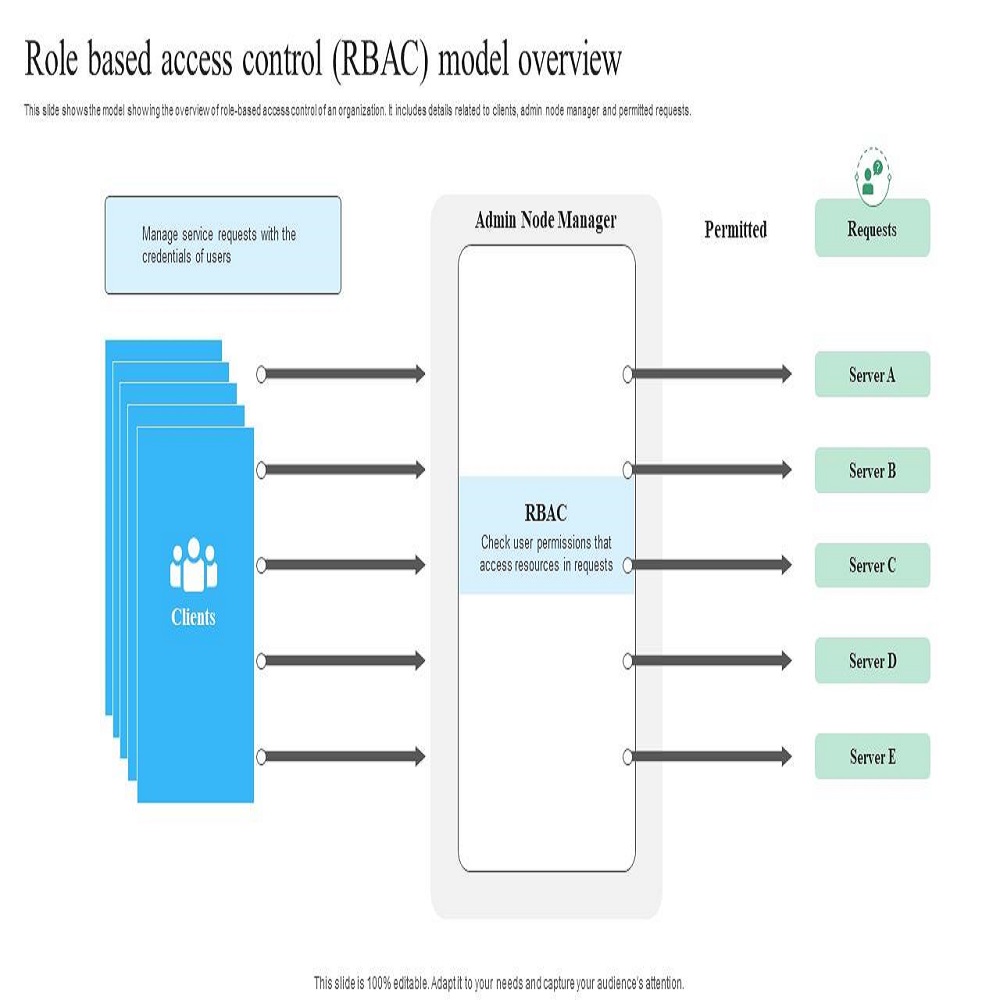
Role-Based Access Control (RBAC)
RBAC attaches permissions to roles within an organization rather than to individual users. It simplifies the management of user privileges and is ideal for medium to large organizations. Access rights are based on a person’s job function, providing a structured and organized way to manage access.
Rule-Based Access Control (RuBAC)
RuBAC adds another layer of depth to access permissions. It sets rules that can change based on certain factors like time or location. This model is highly flexible and can provide dynamic access control based on predefined criteria. It’s especially useful for properties needing timed or situational access restrictions.
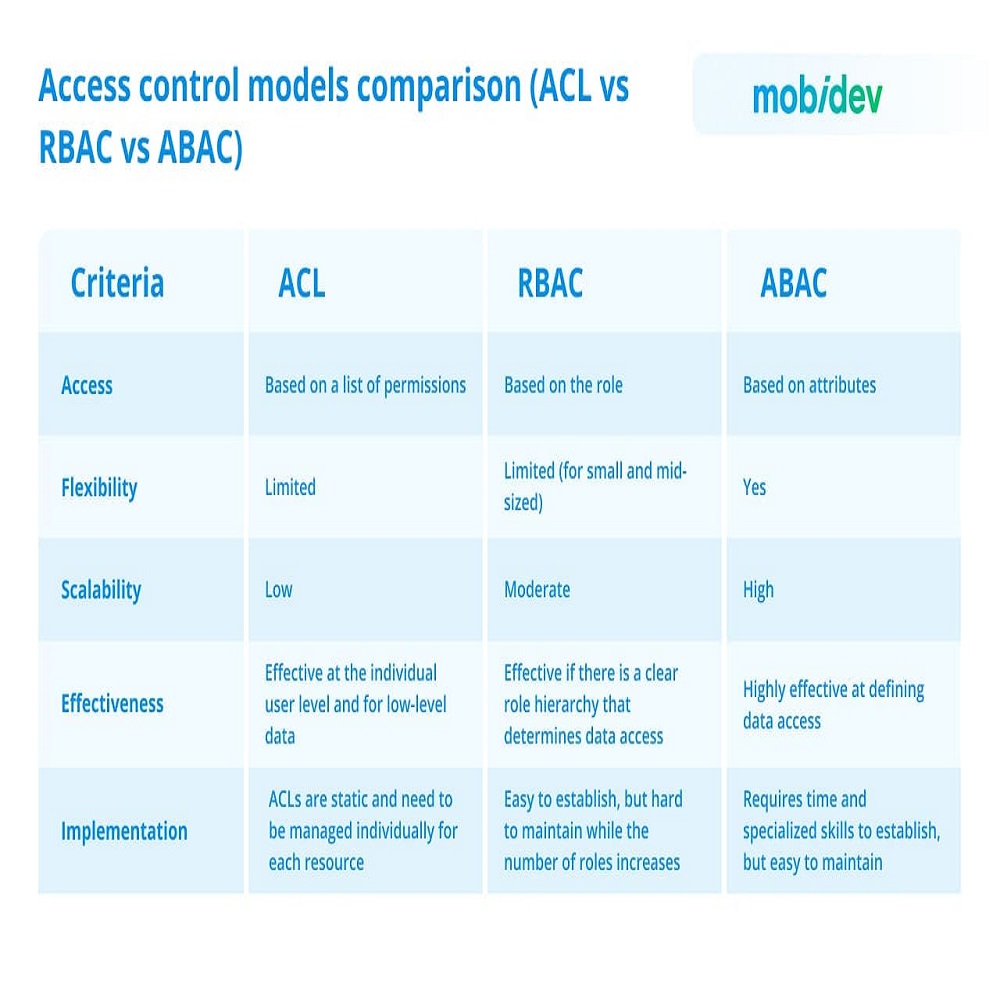
Comparing Access Control Models: Advantages and Disadvantages
Choosing the right access control model depends on several factors. Different models cater to varying needs based on security levels, user management, and flexibility. Below we compare the advantages and disadvantages of the four main access control models to help guide your choice.
Discretionary Access Control (DAC)
Advantages:
- Offers flexibility with multiple admins.
- Easy for users to understand.
- Quick to set up and maintain.
Disadvantages:
- Risk of security breaches is higher.
- Can be problematic if users have too much control.
- Not ideal for high-security environments.
Mandatory Access Control (MAC)
Advantages:
- High level of security with strict controls.
- Ideal for handling sensitive data.
- Centralized management simplifies oversight.
Disadvantages:
- Processes for changes can be slow.
- Less flexible for users needing varied access.
- Can be complex to set up.
Role-Based Access Control (RBAC)
Advantages:
- Simplifies permissions by role.
- Scalable for growing organizations.
- Easier to audit and comply with regulations.
Disadvantages:
- Roles must be well-defined, which can be difficult.
- Changes in roles require updates to access rights.
- May not fit organizations with fluid job responsibilities.
Rule-Based Access Control (RuBAC)
Advantages:
- Allows dynamic access based on rules.
- Can adjust to situations like time of day.
- High-security use in sensitive areas.
Disadvantages:
- Can be complex to set up and maintain.
- Needs constant updates to rules as situations change.
- May be too granular for some users’ needs.
Each model presents its own benefits and challenges. It’s essential to weigh them according to your specific needs. Consider user experience, security requirements, and the ease of managing the system when selecting an access control model.
Criteria for Selecting the Right Access Control Model
Choosing the right access control model is key to protecting your property effectively. To select the most suitable model, consider the following factors:
- Security Requirements: Assess the level of security your property needs. High-security areas may need a MAC or RuBAC model.
- User Management: Think about who will manage user access. If multiple administrators are involved, a DAC might be convenient. For role-oriented management, RBAC is ideal.
- Flexibility Needs: Evaluate if your organization requires a flexible approach. DAC offers more user control but may increase security risks.
- Scalability: Plan for growth. RBAC scales well with your organization’s size and complexity.
- Audit and Compliance: Check for access models that support compliance with regulations. RBAC often meets these requirements.
- Ease of Implementation: Consider how easy each model is to set up. If DAC meets your needs, it can be quickly implemented.
- Maintenance and Updates: Assess how often your access needs change. Models like RuBAC may need regular rule adjustments.
- Dynamic Needs: If access requirements change based on conditions like time, RuBAC provides dynamic control.
- Environment: The type of property you have will influence your choice. Commercial properties tend to have different needs from residential buildings.
- Budget Constraints: Factor in the costs associated with each model, as some may require more investment.
By considering these criteria, you’ll be well on your way to selecting an access control model that best fits your property’s needs and characteristics, ensuring user-friendliness and security.
Role-Based Access Control: The Preferred Model for Many
Role-Based Access Control, or RBAC, stands out as a popular choice. It aligns permissions with organizational roles. In RBAC systems, user accessibility hinges on their job functions. RBAC offers structure. It simplifies managing large user groups. It also makes auditing more straightforward.
RBAC’s design resonates with many organizations for its clarity and efficiency. It minimizes confusion. Each role has clearly defined privileges. This makes it easier to control access. Users understand their boundaries. Admins enforce security measures effectively. Onboarding new employees becomes less complex. Admins assign them a role that automatically confers the needed rights.
Another advantage is its scalability. RBAC evolves as the organization grows. Adding new roles or adjusting permissions is straightforward. It adapts to complex or changing structures without hassle. This model also supports compliance with regulations. It offers transparency for every user’s actions.
For all its benefits, drawbacks exist. Roles must be accurately defined. If roles change, access rights need updates. Organizations with fluid job responsibilities may find RBAC challenging. It’s important the chosen access control models fit the organization’s operational flow. Overall, RBAC balances usability and security effectively, making it a favored model for many.
Implementing Access Control Models in Various Organizations
Choosing the right access control model is vital for any organization. The model you select should align with the nature of your business. It should also meet its specific security needs. Here’s how different organizations might implement these models.
Discretionary Access Control (DAC) in Small Businesses
Small businesses often choose DAC for its simplicity. It allows them to quickly adapt to changes in their structure. Owners or managers grant permissions directly. This keeps the process clear and manageable.
Mandatory Access Control (MAC) in High-Security Environments
MAC is more suited to environments where security cannot be compromised. Government bodies and military facilities often use this model. It ensures that only those with the correct clearance level access sensitive data.
Role-Based Access Control (RBAC) in Medium to Large Organizations
Medium to large organizations benefit from RBAC. It makes managing access rights easier across various departments. Job roles link to specific access permissions. It streamlines the process for assigning and revoking rights.
Rule-Based Access Control (RuBAC) in Dynamic Settings
Organizations with dynamic access needs might prefer RuBAC. Schools can restrict classroom access during off-hours. Businesses can limit entry to certain spaces based on time or event triggers.
When you implement these models, consider user needs and security demands. Plan for potential growth too. This ensures that your chosen model can evolve with your organization.


