Introduction to Rule-Based Access Control
Rule-Based Access Control (RuBAC) is a way to manage who can go where or do what in a system. It sets rules that must be followed for access to be allowed. These rules are based on details like time, location, and job activities. RuBAC is not the same as Role-Based Access Control (RBAC), which looks at a person’s job in an organization. Instead, RuBAC sets specific conditions for access.
Characteristics and Functioning of Rule-Based Access Control
Rule-Based Access Control (RuBAC) operates on a clear set of directives. These directives dictate access rights for users across various scenarios. Unlike systems that depend on a user’s role, RuBAC applies strict criteria to manage entry to secure areas and data. Here is how it functions in a system:
- Access Trigger Points: RuBAC systems activate when a user attempts to access a protected resource. The system evaluates the request against a series of established conditions.
- Defining Rules: Administrators set specific conditions, which could be based on time-of-day, location, or user activity. These predefined rules lay the groundwork for the RuBAC framework.
- Dynamic Responses: Upon a user’s access attempt, the system checks if the criteria meet the set rules. If they align, the system grants access; if not, it denies entry.
- Flexible Criteria Application: RuBAC can adapt to various operational needs. This may involve restricting access after business hours or limiting entry to certain roles during high-risk periods.
- Exception Handling: Exceptions to the rules can also be programmed. This ensures that, even within a rigid structure, there can be room for necessary deviations.
In essence, RuBAC is about setting a concrete security infrastructure that navigates the complexities of access management while offering a tailored control mechanism to protect sensitive assets and areas.
Benefits of Implementing Rule-Based Access Control
The adoption of Rule-Based Access Control (RuBAC) in a security system brings clear perks. Here are some key benefits:
- Enhanced Security Levels: RuBAC provides extra layers of defense. It sets strict rules that help prevent unauthorized access.
- Customizable Rules allow admins to tailor security measures. They can adapt rules to fit different scenarios and changing threats.
- Efficient Access Management: The system can process requests fast. Once set, the rules quickly determine if access should be granted or denied.
- Compliance with Regulations: RuBAC can ensure that access policies comply with legal standards. This is vital for industries with strict regulations.
- Operational Flexibility: Unlike rigid role-based systems, RuBAC can offer more nuanced control. It can restrict or allow access based on various factors like time or risk levels.
- Scalability: As an organization grows, RuBAC can easily expand. It can handle an increasing number of users and complex access scenarios.
However, it’s important to balance these benefits with the potential for complexity. Admins need to carefully manage and review the rules to keep the system running smoothly.
Potential Drawbacks and Challenges of Rule-Based Access Control
While Rule-Based Access Control (RuBAC) offers many advantages, it also presents several challenges. Complex Setup is a major concern as it requires careful planning and detailed rule setting. This can be time consuming and demands a deep understanding of the organization’s needs and potential risks. Maintenance Effort increases with the complexity of rules; administrators need to regularly review and update the rules to ensure they remain relevant and secure. Limited Flexibility may arise because once rules are set, they can be inflexible. Changes in the organization’s operations might require rule adjustments that are not easily made. Risk of Errors in the configuration can lead to security breaches or denial of legitimate access. Keeping rules error-free and up to date is crucial yet challenging. Resource Intensity is another challenge as more complex RuBAC systems may require significant processing power, especially in large organizations with high transaction volumes.
Thus, it is clear that while RuBAC systems are powerful tools, they must be managed carefully to avoid potential pitfalls. Effective implementation and consistent management of rules are key to harnessing the benefits while mitigating the challenges associated with RuBAC.
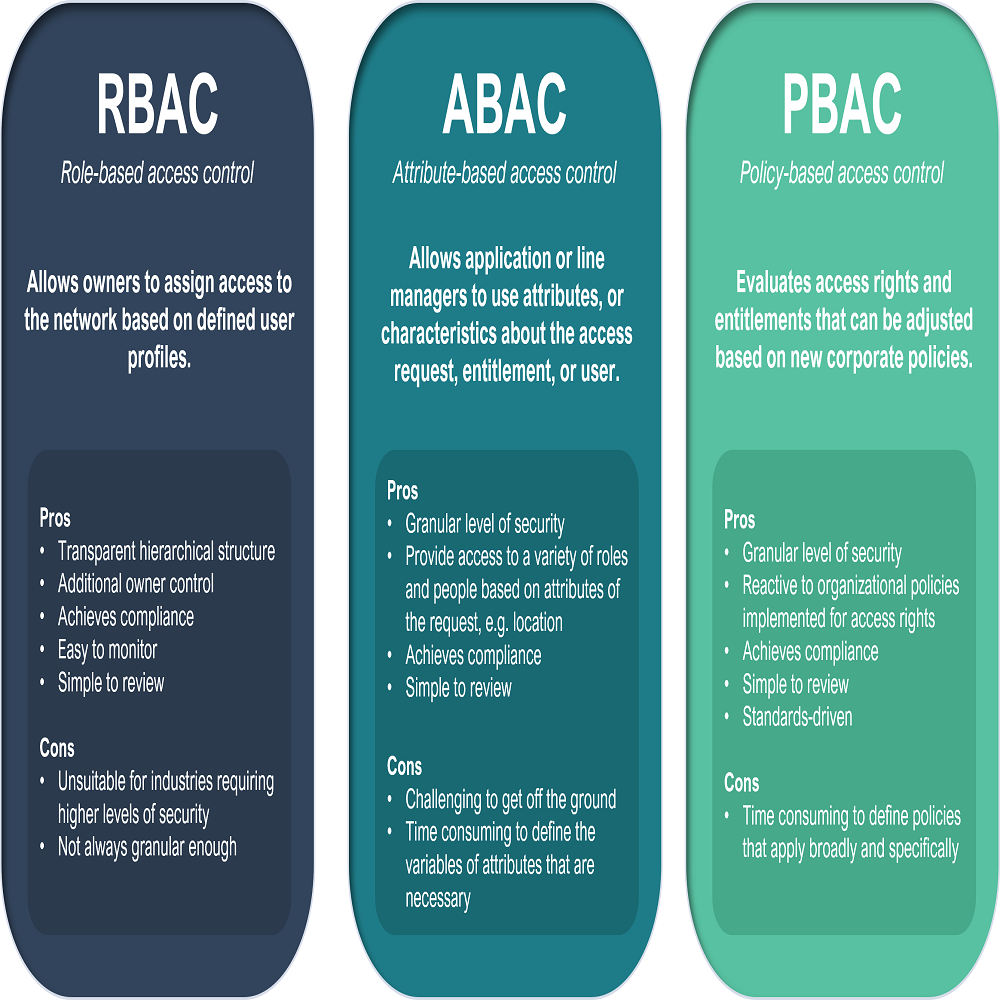
Comparison: Rule-Based vs. Role-Based Access Control Models
When keeping a space secure, how you decide who gets in matters a lot. Two common ways are Rule-Based Access Control (RuBAC) and Role-Based Access Control (RBAC). They are not the same, even if they sound alike. Here’s how they stack up against each other.
- RuBAC: Think of RuBAC like a bouncer with a list of rules. If you don’t fit the rules, you can’t enter. It looks at things like ‘What time is it?’ or ‘Is this place already too full?’ to make decisions. It’s very specific and flexible but can get complex.
- RBAC: RBAC is more about your job in the place. If you are a manager, you get keys to more doors. It’s simpler to handle but not as detailed as RuBAC. Changes in job roles mean changes in access.
Here are some things to think about:
- Decision-making: RuBAC acts on preset conditions, while RBAC looks at a user’s job title.
- Complexity: RuBAC rules can cover more ground but might be tougher to keep track of. RBAC’s role-based rules are easier to manage.
- Changes: In RuBAC, you change the rules. In RBAC, you change the roles.
- Size Matters: For a big place with lots of people, RBAC might be easier to use. Smaller or more high-security areas might do better with RuBAC.
Choosing between RuBAC and RBAC means looking at what your organization needs. How big is it? How often do things change? What kind of security risks do you have? Both have their good points, but it comes down to fitting the system to your world.
Implementing Rule-Based Access Control in Practice
When putting RuBAC to use, it’s all about setting clear rules that guide access decisions. Here’s how you can make it work in real-world scenarios:
- Start with a Solid Plan: Pin down which resources need protection. Think about the ‘who’, ‘what’, and ‘when’ of access.
- Create the Rules: Decide on the conditions for access. These could be about time, place, or actions. Make sure each rule is clear and makes sense.
- Test the Waters: Before going live, check the rules. Make sure they do what they’re supposed to and don’t let through what they shouldn’t.
- Train the Team: Help your staff understand the rules. Explain how they affect their work and why they’re important.
- Keep an Eye on Things: Watch how the rules work in daily use. Are they too strict, too loose, or just right?
- Update as Needed: Be ready to adjust the rules. If your business changes, your access control might need to change too.
Implementing RuBAC takes careful planning and constant attention. But get it right, and it’s a strong way to keep your spaces safe.
Best Practices for Managing Rule-Based Access Control Systems
When managing Rule-Based Access Control (RuBAC) systems, follow these best practices:
- Understand Your Environment: Know your space and the risks. Recognize what needs protection and from whom.
- Define Clear Rules: Make rules that are easy to get. They should be direct and match your security goals.
- Keep It Simple: Start with the basics. Use rules that are easy to follow and manage.
- Regularly Review and Update: Check your rules often. Change them as needed to keep up with new threats or changes in your environment.
- Provide Training: Teach staff about the rules. Make sure they know how to use the system and why it’s important.
- Use Automation Wisely: Automate where you can, but keep control. Use tech to handle tasks, but don’t lose touch with the system.
- Document Everything: Keep detailed records of all rules and changes. This helps track down issues and makes audits easier.
- Plan for Emergencies: Have a backup plan. Know what to do if the system fails or a breach happens.
By following these steps, you can ensure your RuBAC system works well and keeps your space secure.
Choosing the Right Access Control Model for Your Organization
Selecting the right access control model is pivotal for your organization’s security. Here are key points to consider:
- Assess Your Needs: Understand the specific security requirements of your organization. Consider the sensitivity of the data, the size of the workforce, and access frequency.
- Evaluate System Size: Bigger organizations with many employees may benefit from RBAC due to its scalability. Smaller, flexible environments might suit RuBAC better.
- Consider Flexibility Versus Structure: Weigh the need for rigid rules against the need for role-based ease of management.
- Think About Compliance: Ensure that your chosen model aligns with industry regulations and standards.
- Plan for Growth: Choose a model that can adapt as your organization expands. Can the system scale without becoming too complex?
- Prioritize Ease of Use: A system that’s too complicated can create a barrier for users. It should enhance security without hindering day-to-day operations.
- Account for Change Management: Look for an access control model that can adapt to changes in roles, responsibilities, and security threats.
By carefully considering these factors, you can select an access control model that fits your organization’s unique context and maintains strong security measures.
Conclusion: The Role of Rule-Based Access Control in Ensuring Security
Rule-Based Access Control (RuBAC) plays a crucial role in security. It sets specific rules that decide who can access what and when. This control level helps protect sensitive areas and data.
Key takeaways about RuBAC are clear. It offers detailed control through well-defined rules. These rules work to manage access across various scenarios effectively. RuBAC systems must align with the organization’s operations and security risks.
Yet, RuBAC can be complex and require steady oversight and updates. This is to respond to evolving threats and changes within an organization. Despite these challenges, when managed well, RuBAC is a powerful tool. It ensures that access to resources is granted properly and securely.
In summary, RuBAC’s role is vital in modern security systems. It’s essential for organizations to choose the right access control model. This choice depends on their specific needs and the security landscape they navigate. With RuBAC, companies can create a secure, rule-defined environment. This allows for the safe granting of access privileges.


