Introduction to Access Control Policy
An Access Control Policy is a vital tool in information security. It limits who can access what data. By outlining explicit permissions and restrictions, such policies provide systematic control over information flow within an organization. They ensure that only authorized individuals have access to sensitive resources, thus securing data from unauthorized breaches.
In today’s digital age, where data breaches are common, implementing an effective Access Control Policy is not just beneficial; it’s a necessity. Moreover, such a policy supports compliance with regulations, preventing legal consequences for data mishandling. Organizations of all sizes and types can benefit from a tailored Access Control Policy to protect their operational integrity.
Key Elements of Access Control Policy
Document Overview and Purpose
An Access Control Policy must begin with a clear overview and a strong sense of purpose. This section sets the scene, telling readers which systems and people the policy impacts. It clarifies why the policy exists, to secure data and manage who has permission to access it. Important for all, it guides users on policy importance and adherence.
Comprehensive Glossary and Definitions
The language in an Access Control Policy can be technical. It’s vital to include a glossary. This part makes sure everyone understands the terms used within the policy. It keeps things clear, as terms might change or new team members might join who are not yet familiar. If a policy is unclear, it will be hard for teams to follow it correctly.
Access Control Systems Overview
An overview of the Access Control Systems is essential. It explains the different systems and techniques used to manage access within an organization. This could be something simple like a password system, to more complex methods like biometric scans. This section describes each system type briefly, ensuring a shared understanding before detailing the more complex aspects of the policy.
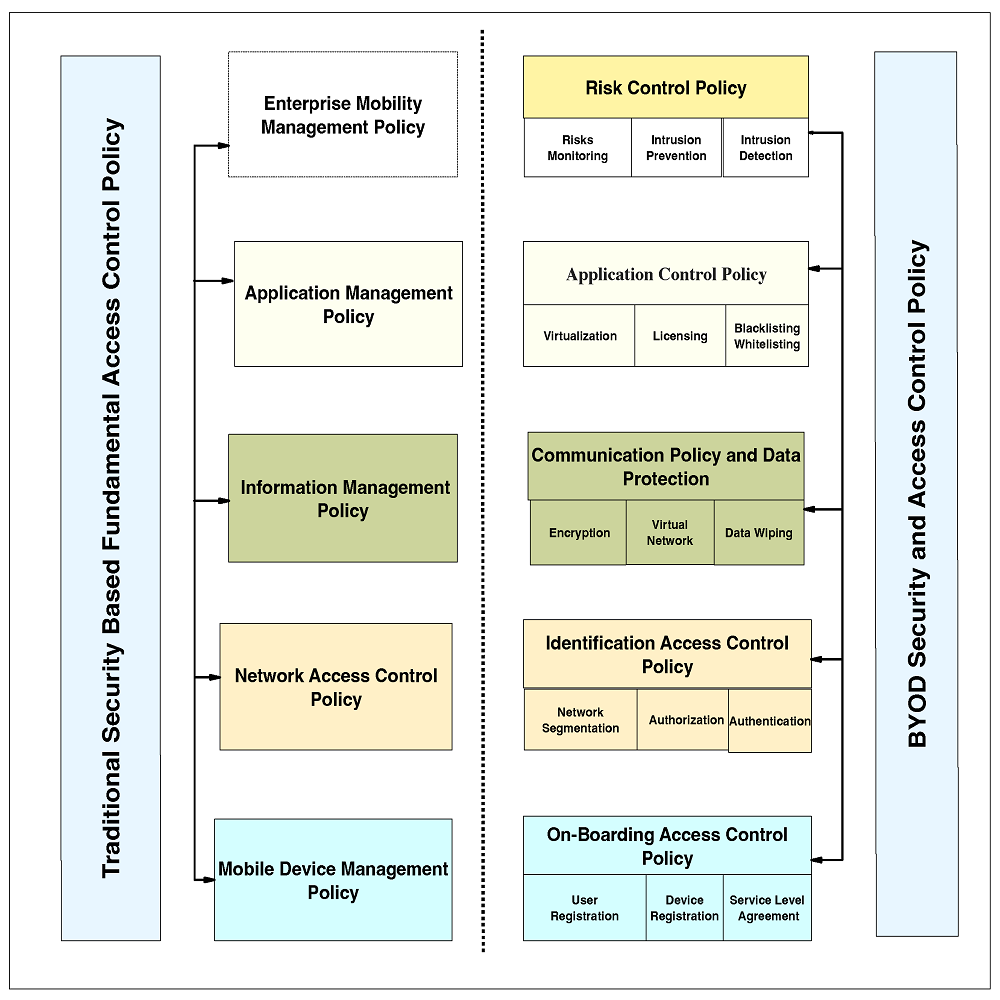
Establishing Your Access Control Framework
To establish an effective Access Control Framework, careful planning and strategic implementation are vital. This framework serves as the backbone for managing how access to information systems and data is granted, monitored, and revoked. Aligning it with the organization’s security policies and compliance requirements ensures a fortified defense against unauthorized access. Your framework should be adaptable, scalable, and capable of evolving with technological changes and emerging threats.
Step-by-Step Guide to Access Control Implementation
Implementing an access control policy involves several key steps:
- Analyze your current security position to understand system vulnerabilities.
- Define roles and access privileges for each level of employee within the organization.
- Install and configure technology solutions like permissions, passwords, and encryption.
- Train staff on safe practices and the importance of following access protocols.
- Continuously monitor and audit systems to ensure the policy is being followed.
These steps constitute the foundation of a robust access control system, addressing various security needs and mitigating risks.
Role-based Access Control Essentials
Role-based Access Control (RBAC) is an efficient way to assign access rights. It groups users based on their roles in the organization and assigns permissions accordingly. This method:
- Simplifies the management of user permissions.
- Enhances security by limiting access to necessary resources only.
- Reduces the chance of accidental insider threats.
- Streamlines user access rights when roles change or employees leave.
RBAC is a dynamic and essential element in access control policy strategies, offering clarity and control over permissions.
Mandatory and Discretionary Access Control Systems
There are two primary systems in access control policy: Mandatory Access Control (MAC) and Discretionary Access Control (DAC). MAC is stringent, as it allows only administrators to manage access rights. DAC is more flexible, permitting resource owners to grant access. While MAC offers high security, it can slow down operations. DAC, though more user-friendly, might require extra vigilance to maintain security. The choice between MAC and DAC depends on one’s security needs, risk appetite, and operational dynamics.

Creating the Access Control Policy
Creating an access control policy demands careful consideration and a systematic approach. Enforcing such a policy ensures that only authorized individuals have the appropriate level of access to sensitive systems and data.
Identifying Information Systems and Data Sensitivity
The first step is to pinpoint which information systems require control measures. Assess the data’s sensitivity for each system. The goal is to protect high-value data from unauthorized access.
Determining Access Requirements
Next, define who needs what level of access. Consider roles, time of access, and user numbers. These factors help set tailored access permissions.
Protecting Data Through Access Control
Once systems and needs are known, decide on control mechanisms. Choose security measures that balance strong protection with needed flexibility for users.
Establishing Rules and Guidelines for Automation
Aim to streamline the policy with clear rules and possible automation. These guidelines help in altering access rights efficiently as roles or staff change.
By recognizing different information systems and their data sensitivity levels, defining access requirements, protecting data with appropriate access control mechanisms, and establishing rules and guidelines for potential automation, organizations can craft a comprehensive access control policy that secures sensitive information while enabling smooth operations.
Documenting Your Access Control Policy
Creating a detailed document is the key to enforcing your Access Control Policy effectively. This document acts as a guide for team members to understand and follow the access rules.
Procedures, Specific Rules, and Compliance Measures
When documenting your policy, it is critical to outline the specific procedures for granting, reviewing, and revoking access privileges. Present clear steps for regular compliance checks and handling breaches. This includes workflow diagrams or step lists for easy understanding. Every rule should align with industry standards and compliance laws to avoid penalties.
Assigning Responsibility: Roles and Departments
Clearly assign responsibility to specific roles within your organization. Specify which departments will oversee the policy’s enforcement and maintenance. Define points of contact for access issues. Having a clear chain of command ensures that team members know whom to approach for permissions and reports. This section should act as a quick reference to facilitate smooth operations.
Leveraging Templates for Access Control Policies
Using templates for crafting an Access Control Policy can greatly simplify the task. It ensures that no critical element is overlooked and establishes a strong structure from the start. Templates offer a foundation that covers the basics of what such a policy should include. This includes roles, data classifications, and access privileges. As a result, organizations can avoid starting from scratch, saving time and resources.
Template Benefits and Where to Find Them
Template benefits are clear. They provide a starting point for policy creation and ensure consistency. Templates also help in complying with industry standards and regulations. Organizations may find templates from reputable cybersecurity firms, government websites, or through professional networks. To find them, one can search online for ‘access control policy templates’ or consult cybersecurity standards organizations like NIST.
Customization of Policy Templates for Your Organization
While templates are helpful, one size does not fit all. Each organization should tailor them to fit its unique needs. Consider the specific information systems, data sensitivity levels, and organizational structure. Customization involves adapting the template to address the roles within the company and the nature of the information processed. Consult with IT and security teams to ensure the template aligns well with current practices and potential threats. This step is crucial for maintaining security and operational efficiency.
Conclusion: The Role of Access Control Policy in Information Security
In wrapping up our discussion on access control policy, its significance in safeguarding information cannot be overstated. A robust policy is the backbone of any organization’s security framework. It serves as a guard, ensuring only the right people have access to sensitive data.
When done right, an access control policy prevents unauthorized access and potential breaches. It is an essential part of an organization’s cybersecurity defenses. Compliance with laws and protection of data are its key benefits.
Moreover, a well-defined access control policy can improve efficiency. It can streamline the process for access requests and changes. This helps maintain a secure environment without hindering productivity.
Across various sectors, from healthcare to finance, a solid access control policy is crucial. It builds trust in an organization’s ability to protect client data and internal information.
In sum, the role of an access control policy is clear. It provides security, complies with regulations, and fosters efficiency. It is not just a document; it’s a strategic plan to keep an organization’s data safe and secure.


